Introduction to AWS IAM: Users, Roles, and Policies.
Amazon Web Services (AWS) offers a robust identity and access management system known as AWS Identity and Access Management (IAM). IAM is a cornerstone for securing AWS resources, providing granular control over who can access your AWS environment and what actions they can perform.
In this article, we’ll explore IAM in detail, covering its key components—Users, Roles, and Policies—and provide practical insights to help you manage access to your AWS resources effectively.
What is AWS IAM?
AWS IAM is a global service that allows you to:
Securely manage access to AWS resources.
Define who (authentication) can do what (authorization) in your AWS account.
Enable users to securely access AWS resources without sharing passwords or access keys.
With IAM, you can create and manage Users, Groups, Roles, and Policies, ensuring fine-grained control over access to your AWS infrastructure.
Key Components of AWS IAM
1. IAM Users
An IAM User represents an individual or a service that interacts with AWS resources. Each user is assigned:
A unique name.
Credentials (password or access keys).
Use Case:
IAM Users are ideal for individuals such as developers, administrators, or analysts who need direct access to AWS.

2. IAM Roles
An IAM Role is an identity that can be assumed by trusted entities, such as:
AWS services (e.g., Lambda, EC2).
Federated users or applications.
Roles do not have long-term credentials. Instead, they provide temporary security credentials for specific tasks.
Use Case:
IAM Roles are perfect for:
Granting an EC2 instance access to an S3 bucket.
Allowing Lambda functions to write logs to CloudWatch.

3. IAM Policies
Policies define the permissions assigned to users, groups, or roles. Policies are written in JSON and specify:
Actions: Tasks that can be performed (e.g.,
s3:GetObject).Resources: AWS resources the actions apply to (e.g., a specific S3 bucket).
Effect: Allow or deny the action.
Policy Types:
Managed Policies: Predefined by AWS or created by the user.
Inline Policies: Directly attached to a single user, group, or role.
Example Policy:

How IAM Components Work Together
Users authenticate with credentials to perform specific actions.
Roles provide temporary access to AWS resources.
Policies define what actions are allowed or denied.
Example Scenario:
A developer (IAM User) needs access to an S3 bucket. Instead of granting permanent access, they assume a Role with a Policy that allows s3:GetObject and s3:PutObject actions.
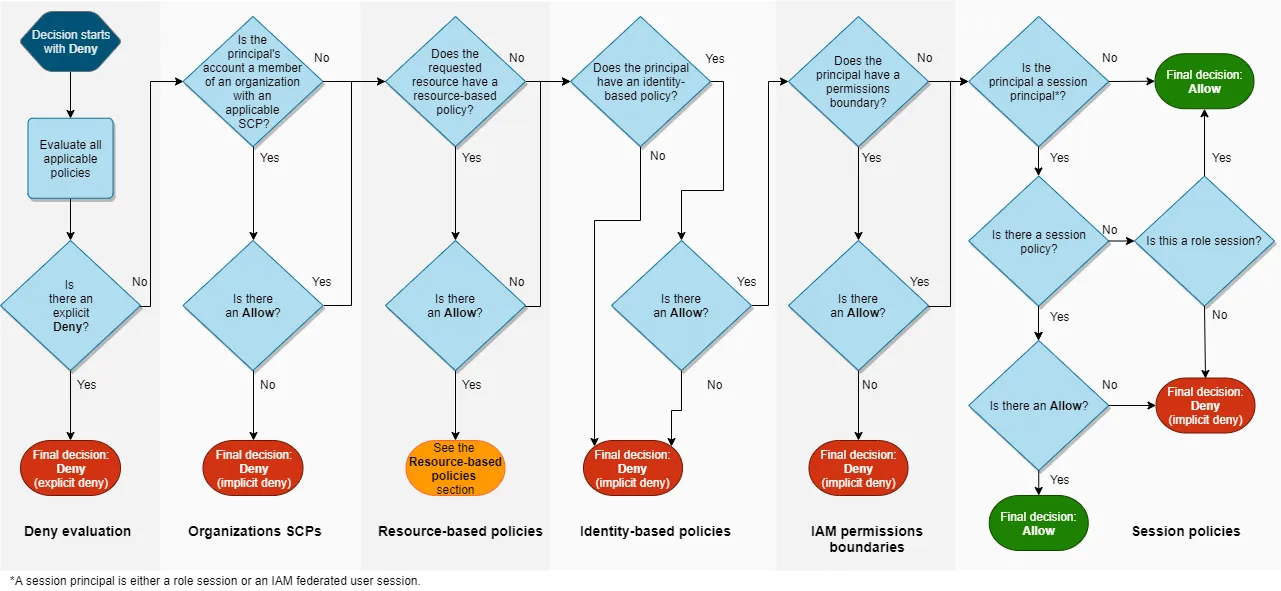
Best Practices for AWS IAM
Follow the Principle of Least Privilege: Grant only the permissions necessary for tasks.
Use Groups for Permissions Management: Assign permissions at the group level to simplify management.
Enable Multi-Factor Authentication (MFA): Add an extra layer of security for all IAM Users.
Use Roles for Applications: Avoid embedding access keys in your applications.
Monitor with AWS CloudTrail: Track all IAM activities for auditing and compliance.
Step 1: Create an IAM User
Go to the IAM Console.
Click Users → Add Users.
Provide a name and select Programmatic Access if you need access keys.
Attach a policy like AmazonS3ReadOnlyAccess.
Review and create the user.
Step 2: Create an IAM Role
Go to the IAM Console.
Click Roles → Create Role.
Select AWS Service and choose the service (e.g., EC2).
Attach a policy like AmazonS3FullAccess.
Review and create the role.
Conclusion
AWS IAM is a critical service for managing access to your AWS resources securely. By understanding IAM Users, Roles, and Policies, you can implement fine-grained access control to ensure your infrastructure is both secure and efficient.
Start leveraging IAM today to build robust access management for your AWS enviro